Disclosure: This post contains affiliate links and we may receive a referral fee (at no extra cost to you) if you sign up or purchase products or services mentioned. As an Amazon Associate, I earn from qualifying purchases.

I spent the last 13+ years of my career in IT as a manager, but I’m still a techie at heart. Even now, almost 7 years into early retirement, I still enjoy keeping up with technology and tinkering with various parts of it.
Over the past few years though, I continue to get increasingly concerned about how we don’t protect our data and identities in the digital world we live in. Privacy and security tend to get put on the back burner.
It’s easy enough to think, “I don’t care if big tech sees my stuff – I’ve got nothing to hide!” It’s also a little comforting to figure that everyone else is in the same boat so why bother changing anything (comfort in numbers)?
Alphabet (Google), Meta (Facebook, Instagram), Apple, Amazon, Microsoft, the big cell phone companies, and plenty more. Too many companies use extensive data collection and invasive tracking practices that are ridiculously commonplace in our digital lives now. Privacy is secondary, if at all.
Then there’s the data breaches. For a while, these were basically treated as a crime against users – the uproar was big, and the involved companies paid retribution to their customers for the failure. Nowadays, you get a letter saying, “All your personal information is now on the internet… sorry about your luck. Here’s a couple of years of useless credit monitoring from a third party that wants to collect your personal information again so they can sell it off.”
Remember the massive Equifax breach in 2017? What do you think happened to them? They essentially got a slap on the wrist and no one was prosecuted. My sensitive data, along with yours most likely, is out there in the hands of crooks. The settlement (which I’m guessing was paid out by their insurance company and not by them) was supposed to get you at most $125 (unless you had claims for additional compensation) but will be much less in the end. $125 maximum payment for all your personal information now made public… not a fair shake if you ask me.
You might think, “Yeah, but what can I do? – I’m no techie!”
I was in the same mindset for a long time except I am a techie and I do know what needs to be done. So I’ve finally started making changes to protect my digital identity and I’ve slowly begun to take my data back. It would be very difficult (and a huge learning curve) to do this all at once, but by doing it one step at a time, I’m happy to be bringing privacy and security back to my digital data.
I’m going to tell you the changes I’ve made so far and what I still want to do. You can do a lot of these things as well and some of them are imperative that you do – the privacy and security of your digital life, which affects your real life, are at stake.
The easy changes for better privacy
To take control of your digital privacy and security, you need to find alternatives that put those at the top of their list in their services. Some changes are easier to make than others. So let’s start with the easy ones…
Change your search engine
I’m going to guess with 81.95% certainty that you’re using Google every time you perform a search on the internet. If that’s the case, know that Google is gathering an incredible amount of data on you that would blow your mind. They use that to continually build a massive profile on you to use for targeted advertising. This takes away your anonymity and is stored on their servers, which is also just waiting for the next data breach or government surveillance request.
Here’s a simple fix… change your default search engine. All major browsers let you easily change which search engine you use.
I’ve been using DuckDuckGo as my search engine for a few years now and haven’t missed Google for search at all. As they say on their site, “Free. Fast. Private.” DuckDuckGo gives me excellent search results and there’s no tracking at all. If you’re unconvinced, try a search at their site and see if it works for you.
Other options you could consider might be Startpage or Brave Search, both of which are private search engines.
If you ever still need to use Google for a particular search, open up a private or incognito window where you’re not logged in and the tracking becomes dramatically less relevant. Also, if your homepage is something like google.com, you’ll probably want to change that, too.
If protecting your privacy and security are a concern (it should be!), this is about the easiest step you can take to move in the right direction.
Use a different internet browser
Here’s another one where big, bad Google carries a ridiculous amount of the market share (almost 70%!). Just like using Google as your search engine, using Chrome as your browser brings about the same privacy concerns. Except Chrome helps ingrain you more in the Google ecosystem making it even harder to get out. If you’re using Chrome on your computer, you’re probably also using Chrome on your phone, too.
I switched from Google Chrome to Mozilla Firefox several years ago and I’m so glad I did. Not only is Firefox a privacy-centric browser, but it’s a lot more extensible and customizable than Chrome – something I definitely appreciate.

It was also a lot simpler than I thought it would be to move. After installing the browser, it provides you the ability to import some or all of these from Chrome (if desired):
- Bookmarks
- Browsing History
- Extensions
- Form Autofill Data
In other words, for the most part, it’s a pretty seamless move – or even just a way to test it out (you can have and use both browsers). The nice thing is that just like Chrome, Firefox has a mobile client (which I happen to like a lot more than Chrome’s) that syncs your data from the desktop browser, too.
I quickly learned to appreciate the customizability of Firefox more than Chrome and I’m glad I made the move. The privacy concern was the driving force but it doesn’t hurt that I like the experience better, too!
Firefox isn’t the only browser focused on privacy and security either. There are others, but the next option I would suggest is Brave. Like almost all major browsers nowadays (including Chrome), Brave runs on Chromium, the codebase developed by Google. That means if things render or work for you on Chrome such as websites and extensions, they’ll almost certainly run identically on Brave.
That’s the good news and I really like Brave, but I still feel too close to Google by using it even though Brave takes the code and modifies it to align with their goals. It’s a great browser though and worth checking out if Firefox isn’t your thing.
Install an adblocker
This is a somewhat controversial topic but installing an adblocker extension is a great way to easily enhance your privacy and security on the web. The most popular ones are designed well enough that the defaults will have you up and running right after the installation in your browser.
At that point, most of the ads you’ll see will disappear when you visit a website. That makes for much cleaner reads… and speedier loading pages!
The controversial part of this is that many sites rely on ads to support their endeavors on the web. For instance, ad revenue accounts for probably around half of the income on my site (which isn’t much regardless). I’m not relying on this income, but adblockers can crush someone’s site who does rely on that.
The reason adblockers are so important though isn’t just about seeing cleaner, faster websites – it’s that they help block trackers and fingerprinting and that’s what you really want. Ever notice how you can look up lawnmowers on a home and garden website and then start seeing ads for them all over the place? Yeah, that’s due to cross-site tracking where you get followed via cookies across multiple websites.
My take is that you should install the adblocker and use it for your privacy and security. If you’re on a site where you want to support the writer or company, just whitelist that site. You’ll then see any ads they have on that site but you’re helping that person or business out.
I’ve been using uBlock Origin for years now and it’s fantastic. uBlock Origin is free and open source and it’s one of the most popular adblockers available. There are others available, too, though. Some of the well-known ones are AdBlock Plus, AdGuard, Privacy Badger, and Ghostery. Outside of uBlock Origin, Of those, I’ve only ever used Ghostery though (which was very good) so I can’t comment on the others.
Now, this is where things get interesting. It used to be that you could install an adblocker on any browser and life was good. But, where does Google make a huge portion of their revenue? Yup, ads. So earlier this year, they changed some of the rules regarding what extensions could do in Chrome that effectively made adblockers, well, not so effective anymore. They’re now extremely limited in how they work.
Remember what I said about changing browsers? Yeah, this is another good reason. So some browsers using Chromium such as Microsoft Edge adopted these new rules (called Manifest v3), while others like Brave and Vivaldi didn’t. Brave, by the way, has its own adblocker built right into it.
That’s another reason why using a browser developing its own codebase built around privacy and security such as Firefox should be considered. This would never have even been on Mozilla’s list of possibilities (unless there were huge security risks) because they’re a non-profit organization not trying to compromise your privacy to make a buck.
Freeze your credit
Identity theft and fraud are becoming so increasingly common now that you need to do the best you can to protect yourself. Luckily, freezing your credit can eliminate almost the entirety of the problem in one fell swoop. Plus it takes only 5-10 minutes to do on the website of each of the three main credit bureaus (Equifax, Experian, and Transunion).
I’m not going to try to reinvent the wheel either. There’s an excellent guide on the Clark Howard website, How To Freeze and Unfreeze Your Credit With Experian, Equifax and TransUnion. It has all the info and links you need. Now you just need to do it. Please do it.
If you need to apply for new credit (like applying for a loan or credit card), it takes two minutes to log in beforehand to temporarily “thaw” your credit. Trust me, we sign up for new credit cards a lot for the travel rewards and it’s a cakewalk to do.
For extra credit, if you have any children, consider freezing their credit as well. This is actually a bigger hurdle to do than it should be, but kids are now a huge target for identity theft and fraud so this is important. I wrote the post Freezing Your Child’s Credit: Why It’s Critical and How To Do It detailing how we got this done for our daughter, Faith.
And, if you want to go above and beyond, you can freeze your credit at a couple of the smaller bureaus as well. I froze each of ours at Innovis and LexisNexis. Again, you can find a great guide on freezing your credit for these and other bureaus on the Clark Howard website with the article, Should I Freeze My Credit With the Other Credit Bureaus?
It’s a no-brainer, folks – a quick privacy and security defense to implement… make it happen!
Check your credit report and set up monitoring
You can and should check your credit report at AnnualCreditReport for free. This is the official government-authorized website. At the time, you could only check your Experian, Equifax, and TransUnion reports for free once per year through the site, but you can now do this weekly.
Look for anything you don’t recognize on these reports or that’s blatantly wrong. If you find something incorrect, follow the instructions to let them know and get it corrected.
I do this once per year. The reason I don’t do it more often is because I have credit monitoring in place to let me know when something changes. My suggestion is to use Credit Karma in addition to or instead of all the free offers you get after the data breaches. This is what I use – Credit Karma is free and works extremely well. It monitors your credit for both Experian and TransUnion. If there’s a change to my credit, I get an email letting me know. If something abnormal shows up, I’ll know it immediately and can get it taken care of before it becomes a big problem.
Quick note – if you’ve frozen your credit, you’ll need to thaw it temporarily when you create your account so it’ll then have access. You only need to do this when creating your account and then it’ll have “permission” to keep an eye on it for you.
Lock your Social Security number
So, if you’re unaware of this other form of fraud, people are now using other folks’ Social Security numbers to obtain work. Fun stuff, right? And, of course, most of these SSNs are coming from data breaches. Assume your info is out there, my friend, because it most likely is.
It’s very problematic if someone reports income under your Social Security number – you don’t want that. The good news is that it’s easy to lock your SSN through the myE-Verify government site.
Here’s another article from Clark Howard’s site that can walk you through the process: Should I Create an E-Verify.gov Account To Lock My Social Security Number? Can you tell I admire what Clark and his staff do? If you listen to one podcast in your life, the Clark Howard Podcast should be the one.
We locked our social security numbers a few months ago. It was easy to do and it’s nice to have another layer of security in place.
Set up an IRS PIN
You may have heard that you should file your taxes earlier than later each year because of tax identity theft or tax refund fraud. Here’s how it works:
- Stealing Personal Information:
Criminals get your personal information (name, Social Security number, etc.) through data breaches, phishing scams, or other forms of identity theft. - Filing a Fake Tax Return:
They use your stolen information to file a fraudulent tax return early in the tax season, claiming a large refund. - Receiving the Refund:
The IRS, thinking the return is legitimate, issues the refund to the fraudster before you even file your real return. - Your Tax Filing Rejected:
When you eventually file your legitimate tax return, it’s rejected because the IRS has already processed a return under your SSN.
Ah, the good times keep on coming!
To fight this, the IRS lets you set up an IRS PIN you need to enter on your tax return when you file. Without the PIN or the wrong one, your tax return gets rejected. The PIN changes every year.
You can get an IRS PIN through the Get an identity protection PIN (IP PIN) page on the IRS website. Be aware that once you have opted in and obtained an IP PIN online, you’ll need to retrieve your IP PIN online each calendar year.
Lisa and I knocked this one out this year as well. Know that getting your PIN is straightforward, but if you don’t already have an ID.me account, that part might take you a little more time. The government’s pushing all their sites to ID.me now though so you’ll eventually need to do this regardless.
Stepping up the privacy and security with just a little more effort
I’m hoping you looked at the low-hanging fruit solutions and are considering trying them out. They’re easy and you can easily jump back to the old way of doing things if you’re not happy.
The next ones involve a little more effort… it’s not too much work though and what you gain in privacy and security relief can make it well worth it.
Use a VPN
If you don’t already know, not only could your browser and search engine be spying and tracking you, but your internet provider could be doing the same. That’s right – in today’s day and age of secure browsing over HTTPS (as opposed to almost obsolete insecure HTTP traffic), your ISP likely can’t see what you’re sending across the internet, but they know every website you’re going to. Oh, and incognito or private browser mode – that doesn’t mean anything to your ISP – they still see exactly where you’re going.
Not only that, but the website you’re going to can see pretty accurately where you’re located.
Changing search engines and internet browsers and using adblockers are one thing, but to push your privacy and security level up a notch, that’s where a virtual private network (VPN) comes into play. A VPN essentially creates a secure encrypted tunnel from you to another endpoint. When you use a VPN, the idea is that no one (not even your ISP) can see where you’re going.
So let’s say you use a VPN and connect to Switzerland with it, all internet traffic is encrypted from you up to the VPN server in Switzerland. The websites you then go to look like they originated in Switzerland so the website servers can’t tell where you’re actually located. And your ISP only knows that you’re using a VPN and that you’ve connected to Switzerland. They don’t see anything else beyond that except perhaps how much data you’re using (if you happen to be downloading a lot, for instance).
So this is a great way to provide more privacy and security to your digital life. Skip the free VPNs – they just aren’t good. They’re almost all very limited, can be frustratingly slow, and they may even be spyware in and of themselves. Plus, the subscription costs for so many of the solid VPNs are extremely reasonable.
I use NordVPN. It’s simple to use, it’s very fast, and it works extremely well. Once you sign up, you install the software on your computer(s), and then just click a button to choose which one of thousands of over 6,800 servers across 111 different countries you want to connect to. That’s it. You can click the button, too, when/if you want to disconnect.
I’ve been using NordVPN for years and love it. As another option, ExpressVPN is a great VPN client as well. Both of these go back and forth as two of the best VPN clients in the industry.
Use a password manager… I mean use it like it’s supposed to be used
Too many folks use the same passwords with all their accounts. That means when there’s a data breach and your info is out there on the dark web (which it pretty much is all but guaranteed to be already), hackers now know the credentials to all your accounts. So instead of one account being at risk, they all are. Not good.
And if your password is still a word or two with a number or maybe an exclamation point at the end, know that it can be cracked in about 2 seconds with today’s technology. Also not good.
If you fall under that umbrella, it’s time to take control. Install a password manager. The ones built into your browser are ok, but not ideal. And what happens when you change browsers like we talked about earlier?
A real password manager can be used regardless of which operating system, browser, or mobile phone you use. They make it extremely easy with browser extensions that can automatically fill in the username and password fields, offer to save new credentials, and even help you generate better passwords.
There are some great ones out there. I moved all of us to Bitwarden a few years ago and I’ve been very happy with it. We’re using the free version but there is some useful functionality that can be gained from upgrading to the paid plan as well.
But that’s the easy part. Once you install a password manager, you need to use it the way it’s supposed to be used. Create a longer, complex master password to open your vault. This is the only password you need to remember, but you want to make it a good one – this is the key to the castle, folks!
Then slowly start changing your passwords for all your accounts… and generate the passwords from your password manager. I’ve recently worked through all my passwords again (I had almost 1,000 different accounts!!) and increased the length to 16 characters. Each of these passwords is a random string of letters, numbers, and symbols that I could never remember on my own… but I don’t need to – that’s why I have a password manager.

Pro Tip: When a website asks you to create security questions like your favorite food, the make of your first car, or your mother’s maiden name, there’s nothing that says you need to give real answers.
Make your favorite food “green couch”, your first car could be “ferris wheel” and your mother’s maiden name might be “I love tacos.”
Put these questions and made-up answers in your password manager so you don’t forget them. And make different ones for every website – that way, if one site gets hacked, that information can’t be exploited on another site. It’s rare that any site needs to know your real information and it’s none of their business anyway.
2FA authentication apps are dramatically more secure than text/email
You know those two-factor authentication (2FA) prompts you get when you log into a website and they send you a code via text or email? Those are better than not having them for sure, but they’re not great. These can be intercepted by hackers through different methods.
On the other extreme are hardware keys you can use like YubiKey that you plug into your computer to present the key. These require physical access to the key itself, which can make them very safe.
If you’re good with the hardware keys, go for it. It’s a very secure solution. For me though, I settled for a happy medium. There are various 2FA authentication apps to choose from that can be installed on your phone to securely provide the rolling codes to you as needed. So right now, when Amazon prompts me for my authentication code, I open the app on my phone, scroll down to (or search for) Amazon, and use the code there. I currently have a little over 100 accounts now set up to use the 2FA app on my phone (which I backup periodically).
I originally was using Authy as my 2FA app. There were various reasons I left but, in a nutshell, I just didn’t like having so much trust for such an important security task in a closed-source app. So I went looking for options and found Aegis Authenticator to be the right answer. This is a great app and extremely easy to use.
I recommend that you install Aegis Authenticator on your phone, but other apps like Google Authenticator and Microsoft Authenticator are popular alternatives. Bear in mind though that the latter two are built by two of the monster-sized mega companies that cause so many of the privacy and security concerns to begin with. Those two are also not open-source apps, so you’re putting all your trust in them to do the right thing. They’re probably perfectly safe, but still worth considering.
Use passkeys wherever you can
In a handful of years, the need to use passwords and 2FA authentication apps should be tremendously less common. That’s because passkeys are the future. I won’t nerd out and go into the technical reasons why they’re so much better, but here are some of the benefits they have over passwords:
- Eliminate password weaknesses
- Resistant to phishing attacks
- Stronger security with public-private key cryptography
- No password databases to be hacked
- Easy to use
- Cross-device compatibility
- Immune to credential stuffing (using leaked usernames and passwords to try logging into other accounts)
- Built for the future and they work well with biometrics
This is relatively new and companies are still working on slowly testing and implementing the technology, but it’s coming in fast. The big companies are on board with it and it’s rolling out everywhere. You can find some of them listed here where you’ll see a lot of the companies you use on a regular basis… Google, Microsoft, Amazon, Best Buy, eBay, Intuit, Kayak, etc.
Here’s the important thing… the passkey needs to be stored somewhere and that’s going to be up to you to decide where. My recommendation is to store them in your password manager (hopefully a standalone password manager) since that synchronizes to all your devices where you have the app installed. I store mine in Bitwarden and that lets me easily utilize them on my computer or phone.
I’ve been using these everywhere I can lately. Try it out when you see the prompt for them or go into a website’s security settings for your account to see if it’s offered.
Email aliases to the rescue
If your email is [email protected] and you use it as your email address/login for every website account, what happens when one of those sites gets breached? Here’s the simple math: the hacker now has 50% of your login for every website you log into. That’s a pretty good head start to hacking into your account, especially if you use the same or weak passwords for your accounts.
Here’s a cool idea – why not use a different email address for some or all of your accounts?
Email aliases let you give out a unique email address that still forwards to your main email address protecting your main email address from needing to be given to another entity (or person). The better ones will let you reply from your alias as well so the receiver never knows your real address.
This also allows you to protect your account from spam. First of all, if you start getting spam on one of your aliases, chances are that the company sold off your email address (jerks!). But second, you can then just disable or delete that alias and suddenly you’ll have no more spam coming in on that alias. Ah, the beauty of a no-spam mailbox!
Your current email provider might already provide email aliases, but I wanted something that wouldn’t lock me into a single mail provider. After trying a few of these, I started using SimpleLogin about a year ago. I also bought a unique domain name for a few bucks a year through NameCheap to use with it. That gives me the portability to take my email addresses with me if I decide to move to another service at some point since I own the domain name and all the email addresses. Right now, that’s unlikely since I really like SimpleLogin, but it’s always smart to ensure you plan for an exit strategy when you start doing anything, particularly with technology.
Now, when I sign up for anything (say Facebook) and it wants my email address, I click the SimpleLogin extension in my browser and generate an email address to use (e.g. [email protected]) and pop that into the website’s form.
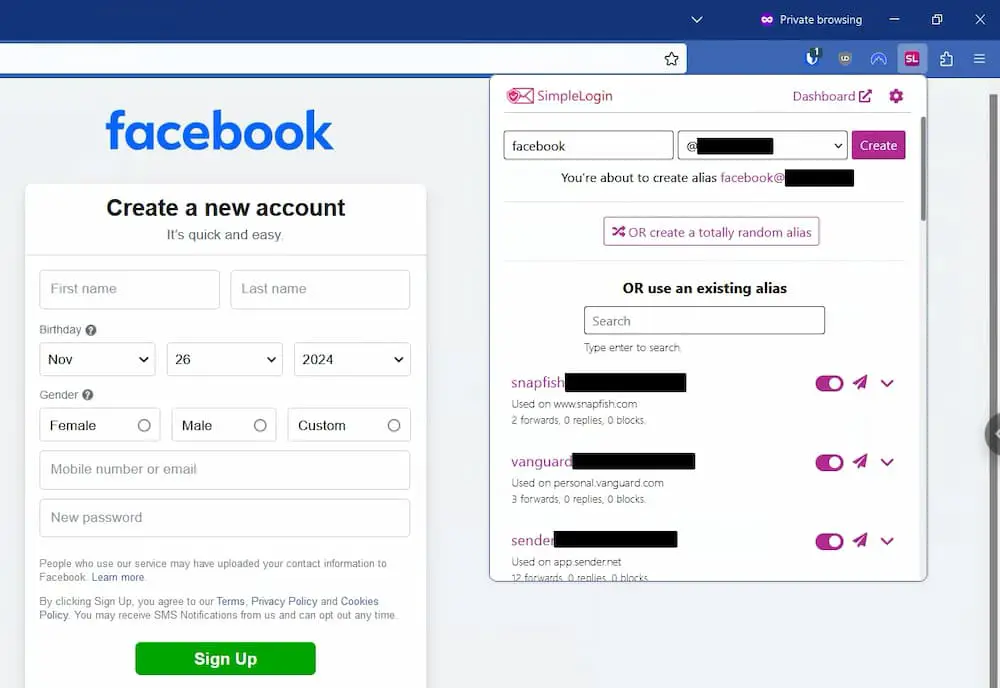
When they email me, it passes through SimpleLogin and then automatically shows up in my regular inbox. When I reply back (from my regular email address), my message goes through SimpleLogin, and they change the message to be from my alias before forwarding it over to the destination.
It took a while, but I’ve moved every account that I have over to an alias now. I’ve also changed email providers (more on that shortly), so now, only friends and family will have my real email address and everyone else gets an alias. That, my friends, is a huge step for privacy and security in a digital world!
I’m very happy with SimpleLogin and since they got acquired by Proton (an excellent privacy-based email company out of Switzerland) in 2022, I’m even more comfortable using them. A couple of other popular open-source alternatives for email aliases are addy.io and Firefox Relay (from Mozilla). I tried out addy.io initially but then switched to SimpleLogin. I can’t remember the reason why but it was something minor that just made SimpleLogin a better fit for me. Either way, they’re both good!
A worthwhile change that involves some work
Ok, now you’ve made it to the point where you’re feeling confident about the privacy and security changes you’ve been making. This was the next thing that I just did that involved some work…
Moving email, calendar, and contacts away from the privacy problem
The heart of the privacy and security dragon that needed to be slayed was my reliance on Google.
You may have heard the saying, “If you’re not paying for the product, you are the product.” Most folks know this is the case with most Google products and services.
Don’t get me wrong – I love most of the Google services available. That’s why I went down the rabbit hole to begin with and it was also the reason I bought their stock so many years ago. But as I’ve taken a step back lately to put more importance on privacy and security, I’m no longer comfortable handing over everything to them.
If you don’t know, Google collects and analyzes the data in your Gmail, calendar events, and contact lists to build a detailed profile of you. This profile can include your habits, interests, relationships, and professional life. Additionally, Google can use all your data to train its artificial intelligence (AI). This scraped data also has the potential for Google engineers to lay their eyes on while refining things.
Now, I get the “I’ve got nothing to hide” mentality, but this level of lack of privacy is simply too much.
So, it was time for a change. I’m so entrenched (and sharing components with family) that moving everything all at once was not realistic. Instead, I decided to break things into smaller chunks that were somewhat linked.
And the first target to move out of Google? I started with our email, calendars, and contacts since those are my biggest concerns. They also overlap in several areas so it made sense to combine them into one project.
I decided that we should buy a custom domain to use regardless of where we went. This would ensure more portability in case we wanted to change providers down the line. It’s easier to move to a new provider then, especially because you don’t need to tell every person and company that you have a new email address. Plus, it’s a little nicer to be something like [email protected] rather than [email protected].
So, after some brainstorming, the three of us agreed on a domain name and I bought it on NameCheap (where I buy all my domains)… sorry, I’m not telling you what it is! 🙂 Then, I started digging into a lot of different services.
The most obvious service was Proton. Proton is a privacy-focused company offering secure, encrypted services like email and calendaring, VPN, cloud storage, and password management, designed to protect user data and promote online privacy.
Try ’em out – they offer free accounts and the services are excellent. They are basically building a Google infrastructure that’s not like Google – it’s centered around privacy and security. The other difference is their business model. They have subscription services rather than making you the product. They’re not cheap either, but if you’re concerned about privacy and security, this should be a company you dig into for sure.
The problem I had was that need to be able to send and receive mail from my routetoretire.com email address as an alias. I can forward the emails to them without a problem, but they don’t support SMTP relaying and I can’t make some technical changes that they would need with the domain to be able to use it there (I won’t bore you with the details). This is unique and not something most folks would run into but it was a dealbreaker for me.
Plus, we’d have to pay for the family plan to share our domain name so we’d be looking at close to $300 minimum every year…
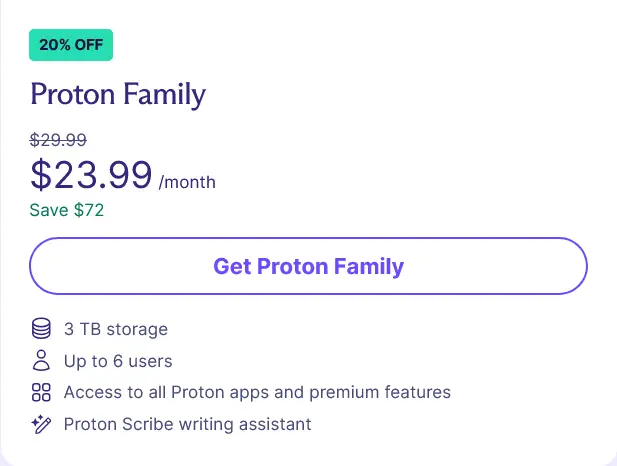
That includes a ton of cloud storage though, but it’s still a tough pill for me to swallow, even if the service is awesome.
So, I had to move on.
I then tried Tuta’s encrypted email, calendar, and contacts. This is a great alternative to Google for better privacy and security, but they just weren’t my cup of tea.
Next, I went to Zoho. Wow, you want to talk about a company that’s built every digital service you can think of under one umbrella? This is the one! Email, calendaring, contacts, online office suite, CRM, social media marketing… over 55 different services!
I’ve actually had a Zoho account since 2009 (I found an old welcome email), but I didn’t really use it much, if at all. So I got to work and got everything all setup. In fact, everything was so far in place that I had set up our new custom domain and migrated us over to it – emails, calendars and sharing, contacts… the works.
I thought we were good but then I started noticing some small details here and there that bothered me.
For instance, there aren’t a lot of fields in their contacts. So when I had imported everything in, if someone in my contacts had more than just a home and work address, it just dropped the other address(es). It also randomly truncated information in other contacts that it didn’t like. That wouldn’t be so bad, but I never got a warning or error message that it was dropping or truncating things. It was dumb luck that I noticed this – it would be a pain to discover missing information later!
I had a couple of other thoughts that were bugging me as well. Nothing crazy and I think that they have some great products, so they’re definitely worth considering. However, I’m very particular about things and it just wasn’t going to work for me.
And so, the day after I migrated us to Zoho, I moved us to another service… Fastmail. And guess what – I love it!
It’s a lot simpler than Proton or Zoho. Fastmail focuses on mail, contacts, and calendars… and that’s mostly it. They have some simple cloud storage and notes but there’s not much to those – likely there to help pacify people requesting it. But everything works extremely well and does everything we need.
Our email all moved over smoothly as did our calendar and contacts (no truncating here!). Our new domain name works well, they provide you with free aliases (though I’m sticking with mine through SimpleLogin for portability), our shared calendaring works great, and our data isn’t being scraped and used all over the place. Plus, I can send/receive from routetoretire.com.
The app is identical to the website (it’s just a wrapper packaging it as an app). But that’s ok because it works great and you have access to everything you can do on the desktop site. Plus, you can use other apps to connect to it. For instance, their app works great for Lisa and Faith but I wanted a different calendar app that would support an agenda widget and a couple of other details. I tried a couple and settled on aCalendar, which does everything I wanted it to do.
And honestly, the pricing is very fair. We’re on the family plan that currently runs $11/month for the three of us. That’s extremely reasonable for everything we’re getting:

So for $132/year, I’ll sleep a little better knowing we’ve got more privacy and security in our digital lives. I’m ok with that!
Moving to a new provider does involve some work, but Fastmail makes it extremely easy. You can go into your account and connect directly to Google to move over your email, calendars, and contacts in one easy step. They’ll even continue pulling from your old email provider if you want until you get all your contacts and accounts using your new email address.
And that’s really the hard part. Changing things over to your new account will take some time and effort. Luckily, while it’s forwarding you can take all the time you need.
I’ve been very pleased with Fastmail, so I contacted them to form a partnership. If you’re interested, you can try out Fastmail for free for 30 days here.
Don’t forget the last step – deleting your data from the old provider! You can still keep your old account (at Google, for instance), just delete the data you’ve moved (mail and calendars in this case). We still need our contacts for our phones since we’re using Google Voice for now, but we’ll be deleting our mail and calendars very soon.
Some changes I still want to make to protect my privacy and security better
Wow, this was a lot to discuss, but I’m not done making changes. As I mentioned, I was so ingrained in Google’s services that I still have more that I want to migrate elsewhere. Some of these include:
- Google Drive and Google Docs/Sheets – I’ll likely be looking to move both of these services to a different solution at the same time since they’re pretty well intertwined.
- Google Keep – It works great, but there are plenty of excellent privacy-based alternatives that do, too.
- Google Maps – There are a lot of good replacements for this one.
- Google Voice – This one is more so because they really don’t give the product much love anymore and the functionality is definitely falling behind.
- YouTube – This should be a pretty easy one.
- Google Photos – if I can find a good replacement that doesn’t involve self-hosting (I don’t want another job)
There will be others on the chopping block, I’m sure, but these are the ones on my mind.
And don’t get me wrong, I still appreciate the products and services that Google makes and I don’t plan to abandon them completely. For instance, I love my Android phone and don’t plan to jump ship anytime soon. I do still use Gemini (Google’s AI chatbot), though I’m really becoming less and less impressed by it compared to others like ChatGPT and Perplexity. And I’m not letting go of my Chromebook anytime soon (though I mostly use it to remote into a Windows desktop!).
The point is that you need to decide what you’re comfortable with and what you’re not. The privacy and security of your data are in your hands to determine what level you want to go to so you can protect it. It doesn’t need to be an all-or-nothing deal either and not everything needs to be done at one time.
As a side note, if you noticed, a lot of what I’ve been switching to are open-source services. That means the code is out there for anyone to review for privacy and security issues. It also becomes a great way for other developers to help contribute to fixes and new features.
In most cases, the services are either free or reasonably priced, too, which doesn’t hurt. I’m a big fan of open-source!
Obviously, I didn’t cover everything here – that would be a book in itself. But these are the changes I’ve been making recently for our own privacy and security and I thought it would be useful for those of you who would like to do something similar.
If you enjoyed this post, jump on the mailing list to be notified about new posts and hear some things that don’t get mentioned on the blog. I’ll send you some spreadsheet freebies that I think you’ll find useful as a welcome gift, too!
Plan well, take action, and live your best life!
Thanks for reading!!
— Jim
Updated on 12/04/2024 to include the section “Check your credit report and set up monitoring.”

Thanks for these comprehensive steps! Our social security numbers were compromised so I have the credit freezes and just recently started working on the SSN lock. I paused when it looked like SS needed to verify identity via Experian so good to know it’s straightforward to temporarily unfreeze. Will look into the IRS pin lock too as that’s one of my biggest concerns. We generally can’t file early due to some of our forms we get generally take longer. Will definitely save this post to come back to!
Thanks Sarah – I would bet that most everyone’s SSN have been compromised now. These breaches have been too widespread and just continue one after another. Looks like you’re on top of things though, which is all any of us can do. Things like the IRS pin lock take a short amount of time to do but it’s nice because it’s just a one time thing to do. Have a great holiday season!
Wow! This is one of the best and most comprehensive articles I’ve read on these measures. I was in the financial services biz before retirement. We were regularly required to take training courses on scams, fraud, privacy, etc. so I’ve had exposure to many of these protections and have employed them but there were many that are new to me. I’m working my way through this list and can’t thank you enough for taking the time to pull all this together and making it understandable to someone who is not a Luddite but definitely not a super technical person.
I’ll be sharing the article to many other folks in my circle who need to be educated on these things.
Thanks again!
Thanks, Lisa – I appreciate the kind words and for sharing the post. I hope you’re able to get some of this fun knocked out! 🙂
Hi Jim,
Are you using Firefox via linux terminal on your chromebook? And if so do you find it as fast as chrome? And with your privacy improments are you considering leaving chrome os for full linux? As I wouldn’t think it will be too easy to leave the Google world while using a chromebook and I have never got a clear answer as to what Google tracks/logs if anything when using linux apps on a CB.
Thanks.
Great question, Lou! I do have Firefox installed under Linux on my Chromebook… but it’s not perfect. It’s a little sluggish at times and, of course, Linux requires some finessing here and there to keep it rolling along smoothly. That said, I also have a Windows PC at home that is our media server. Shortly after I started using Firefox on the Chromebook, I decided to just remote into the PC to run Firefox there… that is pretty close to perfect and I’m happy with that. We’re home most of the time and sometimes I even forget I’m connecting remotely it’s so smooth. I can also access it remotely but then you’ve got latency from the internet so sometimes I’ll just fallback to using it on the Chromebook since everything syncs up to it.
I probably won’t leave Google completely. I love how easy the Chromebook is (especially with what I just mentioned), I love my Android phone, and I love a lot of the Google services. But I do want to be more particular with my data. That’s why we’re now off of email and calendaring (I just deleted all our calendars from Google today). Next will probably be Google Keep and then cloud storage but we’ll see how it goes.
Hi Jim,
Also just coincidentally I read this week your Mint mobile article as I am thinking of switching. And in that post you mentioned using Google Voice for 2 factor authentication. But are you still using GV at all all for that? Or has everything migrated to Authy/Aegis or other authenticator apps? You indicate in this post above that you are not as happy with GV anymore but what specifically do you not like about it? And are there even any other free GV alternatives? And when using GV for 2 factor did you ever encounter any banks or financial institutions or really anything that wouldn’t accept a virtual number for 2 factor?
Thanks again!
Hey Lou – we’re still loving Mint Mobile and it’s definitely worth trying out. We’re also all still on Google Voice. We don’t use GV just for 2FA though – that’s our numbers that we give out and use. It made it tremendously easier while we were in Panama and it’s still great when traveling outside of the U.S.
But it’s got some downsides as well, with the biggest being that Google has all but left it to die. And for as big of a deal as Google has pushed RCS, they don’t support it in GV. So we’re considering porting out (plus, that’s another Google product we get to leave behind).
I do use Aegis for a lot of my 2FA, but there are way too many services that still don’t support anything but SMS codes so most of those go to my GV number. I only have a handful that don’t work with GV so those ones have my actual Mint Mobile number. I just checked and there are 4 that I needed to use my real number with out of all 735 accounts in my password manager so that ain’t too shabby! And only one financial institution out of those 4 (Ally Bank). As a side note, Ally can do email 2FA instead though if desired.
Hey Jim,
Have you checked out DuckDuckGo’s Email Protection? (https://duckduckgo.com/duckduckgo-help-pages/email-protection/what-is-duckduckgo-email-protection/)
I’ve been using it for several years and found it much easier to use than SimpleLogin.
I did try out DDG Email Protection shortly after it came out. I really wanted it to be the answer for me, but it just wasn’t flexible enough for my needs. That’s not too say that’s it’s not a good solution – it is – but I needed some other options. Using my own domain with Simple login has worked great for me, but I can appreciate how DDG is a good service for others… plus $0 is a pretty nice price! 😉